Over the past few years, there has been a significant increase in security breaches, both in terms of frequency and severity. New security tools are flooding the market with the promise of being the next silver bullet. CISOs are left unsure what tools they actually need. Security budgets and tools are ballooning, but high profile breaches continue to happen at a record pace. The reality is that security teams don’t have enough resources to get the most out of their existing tools.
The answer is not creating a bigger SOC with more bodies that prioritize and manage alerts from the endless number of tools you already have. This can actually be counterproductive given the amount of noise and false positives that most tools generate. Manual investigations and remediation is just too error prone and risky. In reality, having just one person or device vulnerable can lead to a breach. The very popular new approach is that SecOps teams are building “self-healing” capabilities into their organization. Here is our definition:
self-heal·ing security
/self-ˈhēliNG/
verb
The ability for an organization to detect and remediate security findings without requiring intervention from the security team.
Example
When a critical vulnerability is detected in a business critical application, the organization self-heals when every person in the workforce applies a patch to the app without manual intervention from the security or IT team.
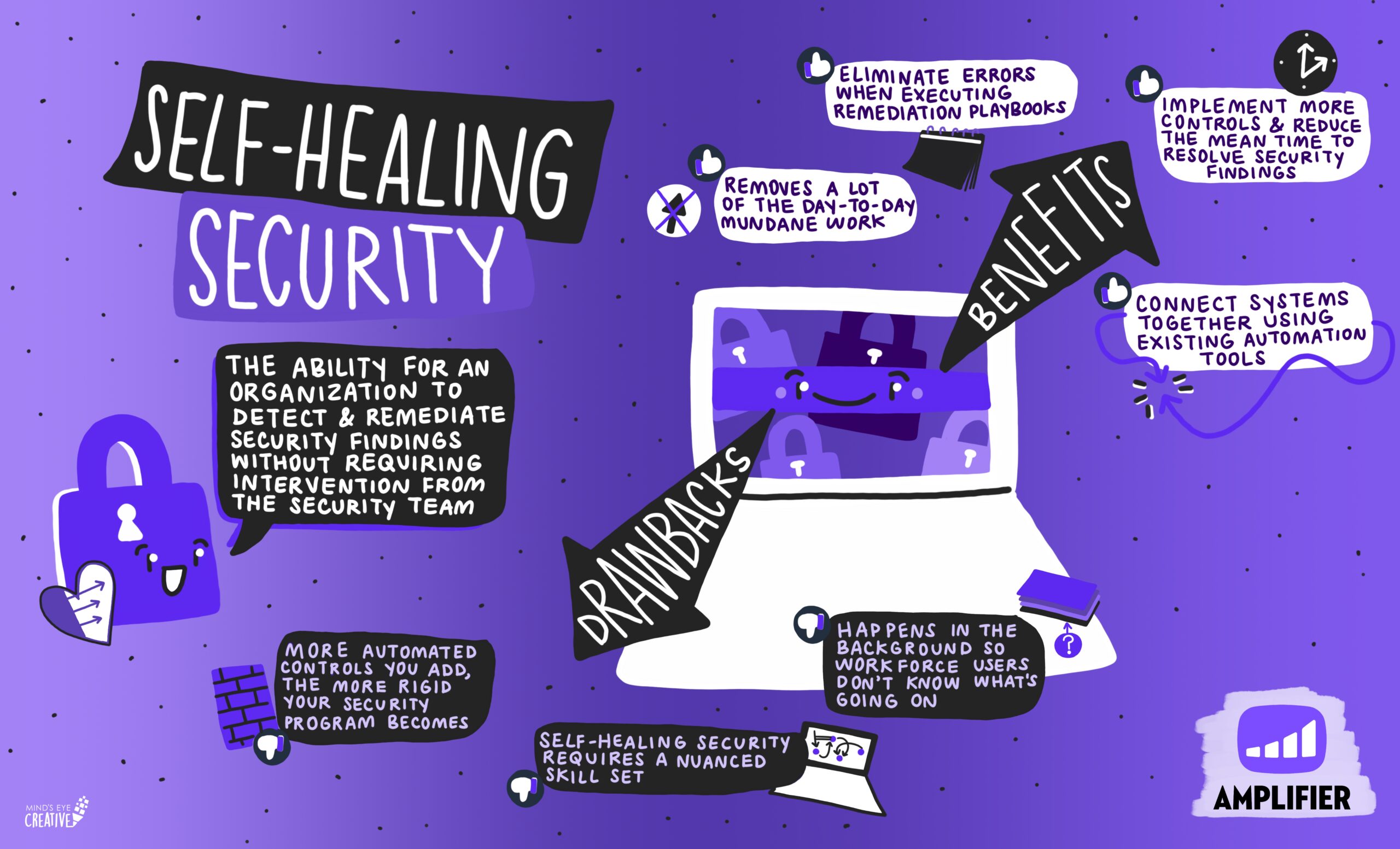
The benefits of self-healing security are significant: SecOps teams are orchestrating remediation of common security findings by connecting systems together using existing automation tools. This allows resource-constrained security teams to implement more controls and greatly reduces the mean time to resolve security findings. It eliminates errors when executing remediation playbooks. And ultimately, it removes a lot of the day-to-day mundane work that bogs down the security team to free them for more strategic initiatives.
Unfortunately, there are some drawbacks to implementing self-healing security systems. As a practitioner, here are some of the most common challenges I have faced:
- The more automated controls you add, the more rigid your security program becomes. In the example above, automatically rebooting users’ computers for a patch can be very disruptive. Blindly automating remediations or blocking access can cause unintended productivity issues and deteriorates the relationship between the employees and the security team. As a result, CISOs are constantly having to balance the tradeoff between workforce productivity and the ability to self-heal.
- Self-healing security is complicated and requires a nuanced skill set that most security teams need to develop; a skill set that includes technical knowledge and business process considerations. Several technical components such as security event ingestion, a security data lake platform, dashboards and remediation scripts have to be integrated with a process workflow to make the ecosystem work. The building and maintenance of these systems and their interdependencies with existing business processes can become time consuming and complicated to handle, particularly given the nuances and fluidity of your organization.
- With automation and self-healing, security happens in the background, so workforce users don’t know what’s going on.The by-product being that self-healing automations can cause a lot of friction – ever experienced unplanned reboots or software updates at inconvenient times? In addition, there is no visibility or context of the “why” for end users, which makes it impossible for employees to understand or learn from security gaps, findings or their mistakes. With this insight, employees can ultimately contribute to a more healthy security-centric culture.
But there is a purple bullet to fix these drawbacks by combining self-healing security with the concepts of human-centric security. In our next blog we’ll dig into the magic that happens when these new concepts meet!

